How Passkeys Work
SnapAuth is based on the Web Authentication (WebAuthn) standard. It offers enhanced security compared to traditional sign-in methods like passwords and one-time codes, while also improving user experience.
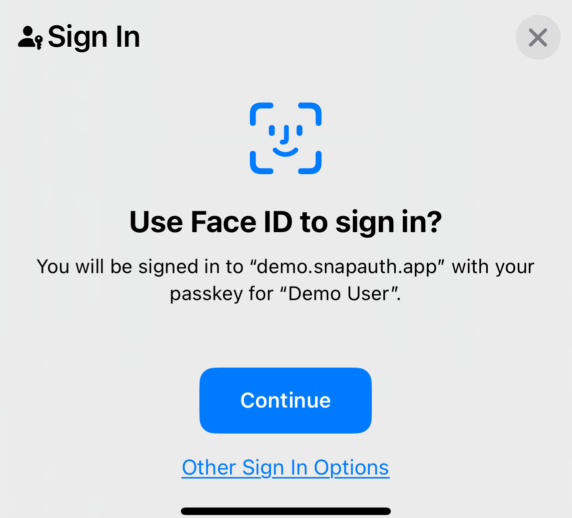
For more about how we protect your data, read about Security at SnapAuth.
Public-key cryptography
Public-key cryptography is a way to secure information by using two separate keys: a public key and a private key.
This is called a key pair.
Both of these "keys" are really big numbers - sometimes hundreds of digits long.
As the name implies, the private key is kept a secret and never shared with anyone else.
It can be used to digitally sign a message that the holder is sending, or decrypt an encrypted message that the holder is receiving.
The public key is safe to send around to anyone.
It's special: it can be calculated from the private key, but the reverse is not true.
If you have someone's public key, you can do two important things:
- Send them an encrypted message that nobody else can read
- Receive a digitally signed message from them and know it didn't come from someone else
The second point brings us to digital signatures.
Digital signatures
Digital signatures are the core of passkeys and WebAuthn. They're like an impossible-to-forge and easy-to-verify version of a wet-ink signature you'd use on a paper contract.
Behind the scenes, there's a whole lot of complex math. But all you need to do is click a button.
Creating a passkey
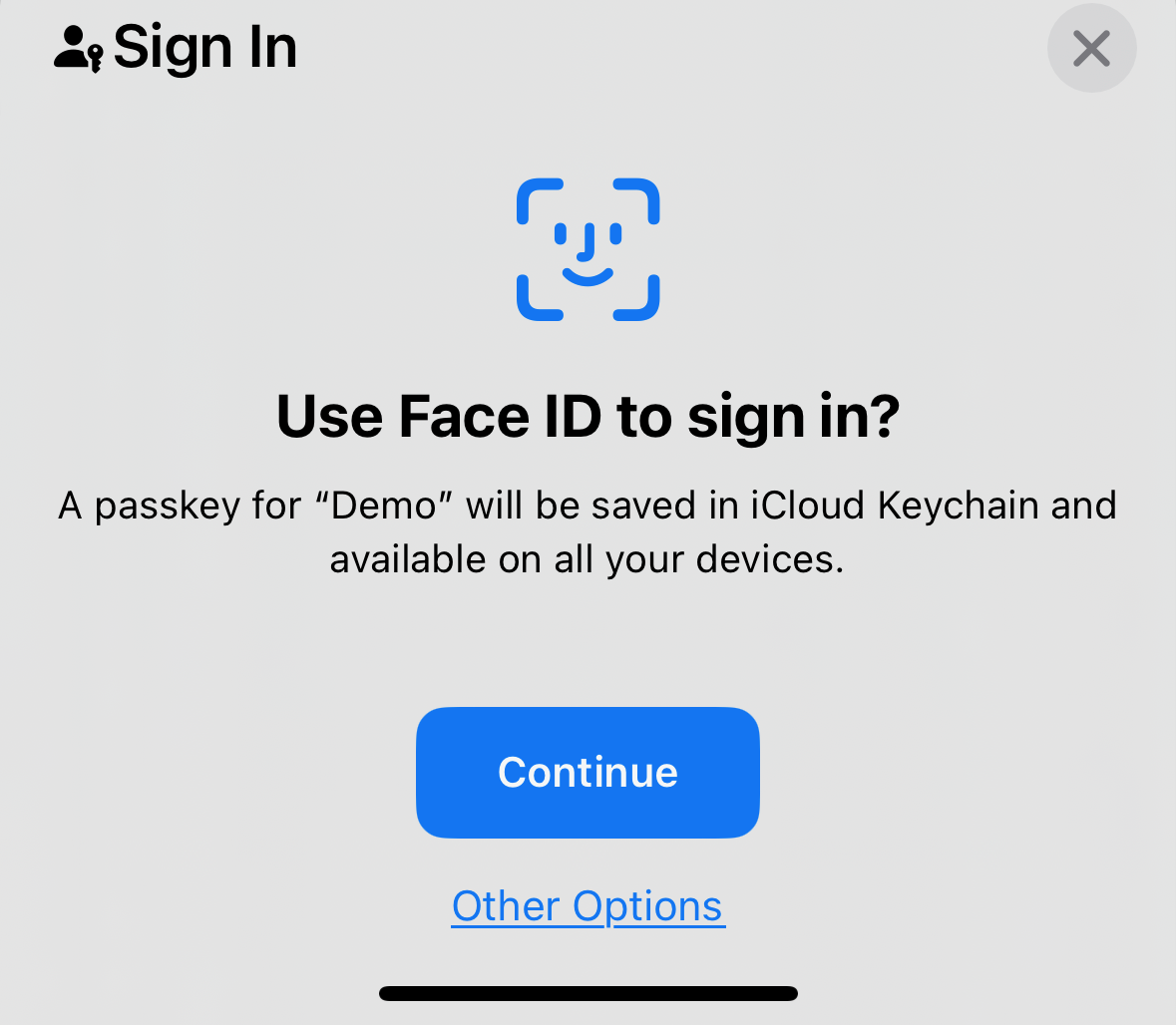
When you set up a passkey on a website or app, you're creating a key pair and sending the public key to that website.
That involves an exchange like the following:
- Alice: "Hi, I'm Alice and I'd like to create a new account"
- Website: "Sure thing. Send me your public key and I'll get you set up. To prove you have its private key, use it to sign this message:
Q_LdYZxcEm2CSQjlcogEPxqhm3XgmgB1gAWWcjmoxO8" - Alice: "OK. Here's my public key:
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEPwmVC/O5OQoXROZAZmqX3eHpoLimrMZCV2N0FIg5pk8BN29DCP7Y1F8M7544KE5Zm/fzzg0+abHlowdH8+W+uQ==, and here's the signature you requested:MEYCIQCY0j2BXLne7WPaasIzEf4a0BwoGpTMsr_vs0OHK0BWyAIhAM0v1z0kncriD_daCyT-q1uClJc0f17p_1awUSxIjVgv" - Website: "Beep boop. That all checks out. I'll keep a copy of your public key so I know it's you in the future."
- Alice: "Thanks! I'll safeguard my private key by keeping it encrypted, that way nobody else can use it."
Signing in with a passkey
When you want to sign in, there's an exchange that looks roughly like this:
- Alice: "Hey, it's me, Alice. I want to sign in to my account"
- Website: "OK, Alice. To prove it's you, use your private key to sign this message:
nWNKhyYeptYPZdsHXipOfia3qt13c6G6HmrJeLwxrf4" - Alice: "Sure, here you go:
MEQCIFwGYTB31-h67TfTij3M-JIWbS0qiMVruplCP2W0Kej3AiAYEZiw7paKT1fqcRD7sMrk4XQdPZxEBCdf7Jw7xK402w" - Website: "Great! I looked up your public key, and confirmed that matches. It must be you, so I'll sign you in."
Passkeys are more secure than passwords
Passwords are, at their core, a secret shared between two (or more) parties. The basic premise goes back thousands of years1, and have been used in computing since the start of the industry.
The problem with secrets are, of course, that sometimes they stop being secret. Passkeys make this problem obsolete.
Unlike using passwords, secret information never leaves your device when signing in with a passkey.
The private keys for passkeys are kept top secret by your operating system.
Nobody else can leak or misuse them, because they never get them.
They're also always unique to every website you use. This is both safer and more private: nobody can know what other websites you use by knowing one of them.
If a site you're using suffers from a data breach, your passkeys on that site will not compromise your accounts on any other sites.
And since they're specific to a website, it means they're extremely phishing-resistant.
Passkeys DO NOT share your fingerprint or face data
As you saw above, passkeys can let you sign in to a site using Face ID®2 and other biometrics.
That data is top secret and never leaves your device.
What's happening is your operating system verifies it's you using your device again, using a fingerprint or face scan, the same way you already unlock your phone or computer. If your device confirms it's you using it, then it decrypts the private key for the website, performs the digital signature, and encrypts the key again.
At no point does a website or app ever get your fingerprint or face scan when using passkeys. It is entirely device-local.
Batteries included
You don't need to install any new apps to use passkeys - they're already supported by the operating system and browser you already have.
When creating an account or signing in to one, you stay where you are. No need to open up a password manager or switch to your text messages to enter a one-time code.
Try passkeys today
If you're a person learning more about passkeys and this sounds better than passwords (we certainly think they are!), share this page with your favorite websites. We'll help them support passkeys, so you can have a safer experience and never enter a password again.
Want to try it out? We have a live demo at https://demo.snapauth.guide. (It won't add you to a mailing list or even ask for an email address)
If you're running a website or app, SnapAuth makes it super easy to add passkey support. Sign up today for free, and contact us with questions or if you need help.
Face ID is a registered trademark of Apple. Its use in this article does not constitute their endorsement of our services. Passkeys work on non-Apple devices, such as Android phones and Windows PCs. ↩
 SnapAuth
SnapAuth